I’ve been experimenting with Wireguard as a VPN to protect my internet traffic from local snoopers and communicate between all my devices as if they were on the same network.
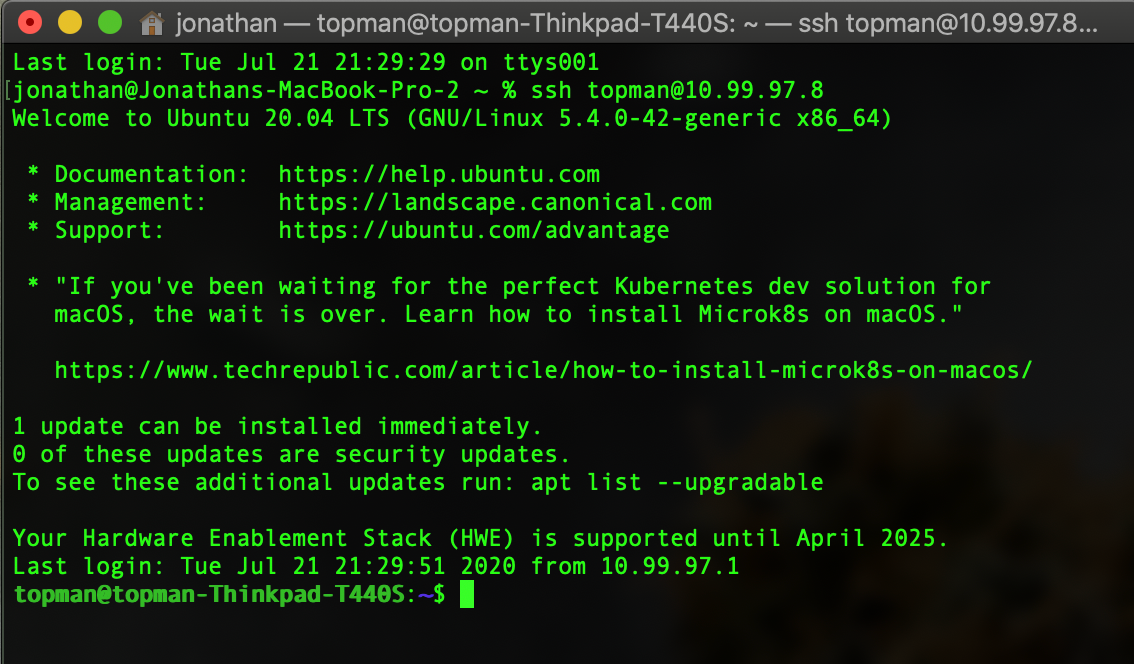
SSHing into an Ubuntu 20.04 Thinkpad on my home network via the VPN.
Wireguard was designed with mobile devices in mind. It uses battery-friendly cryptography and the protocol can handle endpoints that change IP address seamlessly. It is ideal for exposing local development servers on my laptop to my iPhone, but deploying configuration to a device is a manual and time-consuming process.
WireguardHTTPS is a Wireguard access server written in Go that allows users to log in with Azure AD and manage access to the Wireguard VPN.
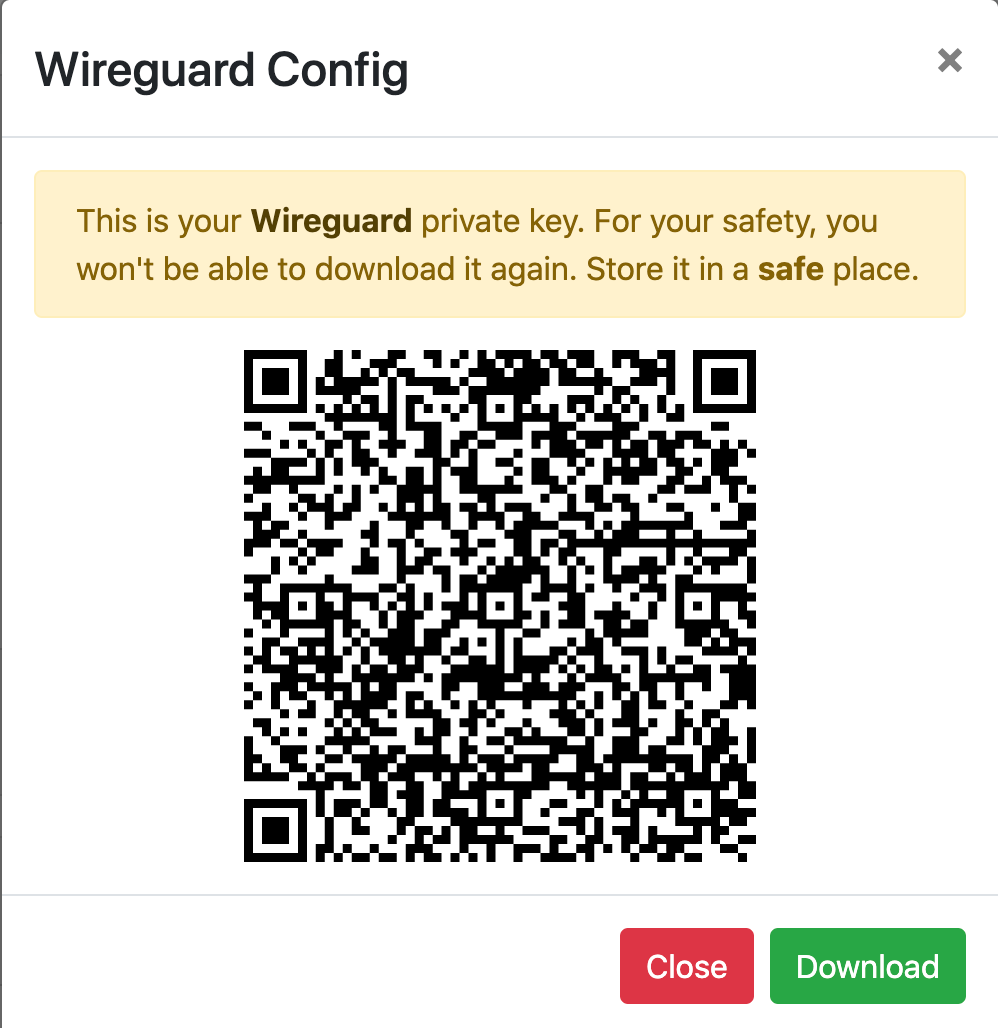
WireguardHTTPS generates configuration and creates QR codes for easy deployment to mobile devices.
WireguardHTTPS is intentionally very simple. It only allows users to add devices to the VPN, regenerate device credentials and remove devices from the VPN. WireguardHTTPS does not store private keys: once a device has been created, future attempts to download its credentials will revoke the device’s access to the VPN and generate new credentials.
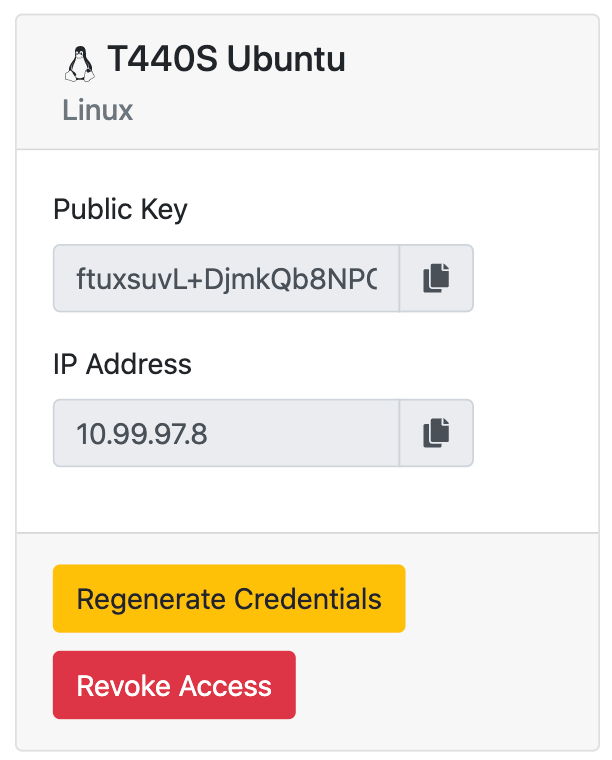
WireguardHTTPS only allows regenerating credentials and deleting a device.
Devices are automatically assigned IP addresses in the subnet specified when setting up WireguardHTTPS. When a device is deleted, its IP address is released for reuse by a future device.
Architecture
WireguardHTTPS is made of 3 components to limit privileges required by the internet-facing HTTPS API while allowing it to control the higher privileged Wireguard interface and protect users from common web attacks like XSS, Clickjacking, and CSRF.
A root gRPC daemon, wgrpcd, controls the Wireguard interface. Wgrpcd manages devices directly on the Wireguard interface using wgctrl and responds to gRPC messages from other processes. It is not aware of IP address allocation, DNS or Azure AD users. It simply validates input received from its gRPC API and manipulates peers on the Wireguard interface.
A low privileged user runs WireguardHTTPS, a REST API that provides authentication, IP address allocation, device DNS settings, and device management. It is exposed directly to the internet without a reverse proxy. WireguardHTTPS allocates IP addresses in its database from a subnet provided by the user at setup. WireguardHTTPS assigns devices IP addresses from this pool, and a device’s IP address is released when it is deleted. It uses wgrpcd’s gRPC API to perform the desired operations on the Wireguard interface. PostgreSQL transactions ensure Wireguard interface and database are kept in sync to avoid IP address conflicts and stale data. WireguardHTTPS does not store any identifying information from users apart from their authentication provider ID, and can easily be modified to support other OpenID providers like AWS Cognito.
WireguardHTTPS is meant to serve its UI: wgreact, a ReactJS single-page app. It uses Gin’s static file server middleware to serve the final Javascript application generated by webpack with a restrictive Content Security Policy, anti-framing headers, anti-XSS headers, and a limited set of TLSv1.2 and TLSv1.3 cipher suites. It is a single page and allows users to add, view, rekey, and remove their devices.
Use Cases
Expose services in private networks to connected devices, even if they’re behind a NAT or in a private VPC. You can host an instance of Gitlab on a computer at home to create a private source code repository and much more.
Move unencrypted traffic from untrusted networks to cloud networks to protect against man in the middle attacks.
Use a static IP address from any network, even on a cell phone.
Source Code
This entire setup is open source. You can see the source code for wgrpcd, WireguardHTTPS and wgreact on Github. WireguardHTTPS is still under development and has not yet been audited. I don’t recommend using this software for anything important. “WireGuard” and the “WireGuard” logo are registered trademarks of Jason A. Donenfeld.” You can download Wireguard at https://www.wireguard.com/